Jan20
40 Million Credit Cards — I.
Editor’s Note
The image may be downloaded in higher resolutions:
↓ Transcript
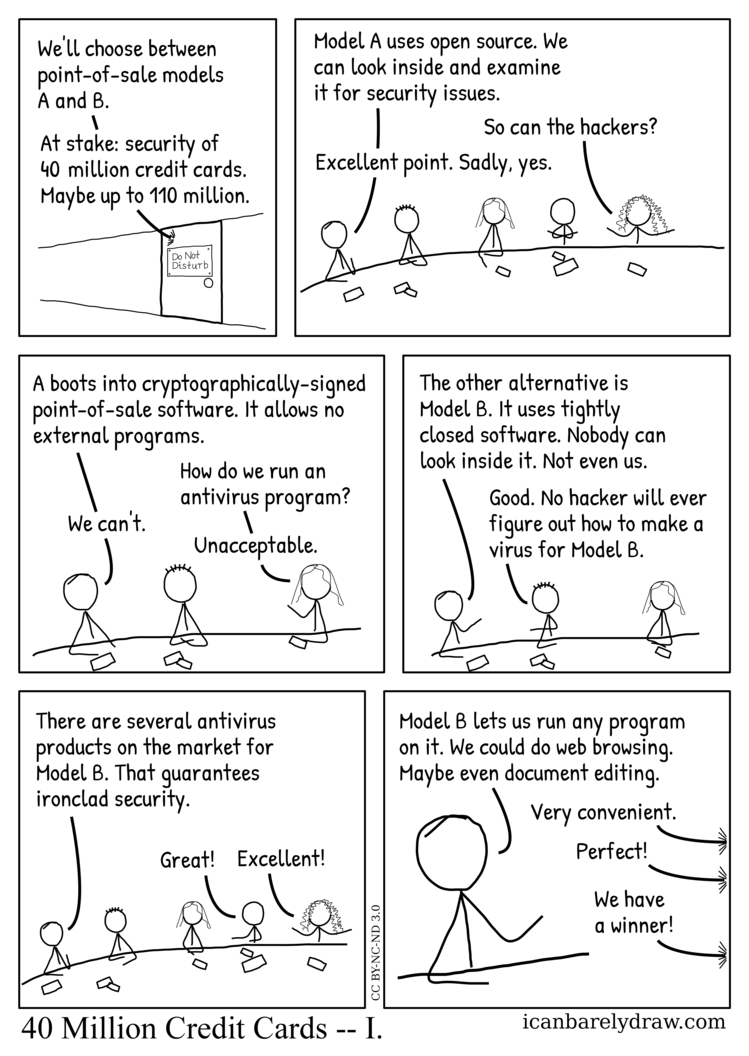
A closed door has a sign that says: DO NOT DISTURB.
Voice from door: We'll choose between point-of-sale models A and B.
Voice from door: At stake: security of 40 million credit cards. Maybe up to 110 million.
The next panel shows a number of people sitting at a circular table. In order from left to right, they are: man 1, man 2, woman 1, man 3, and woman 2.
Man 1: Model A uses open source. We can look inside and examine it for security issues.
Woman 2: So can the hackers?
Man 1: Excellent point. Sadly, yes.
The conversation continues across several panels.
Man 1: A boots into cryptographically-signed point-of-sale software. It allows no external programs.
Woman 1: How do we run an antivirus program?
Man 1: We can't.
Woman 1: Unacceptable.
Man 1: The other alternative is Model B. It uses tightly closed software. Nobody can look inside it. Not even us.
Man 2: Good. No hacker will ever figure out how to make a virus for Model B.
Man 1: There are several antivirus products on the market for Model B. That guarantees ironclad security.
Man 2: Great!
Woman 2: Excellent!
The next and final panel shows only man 1.
Model B lets us run any program on it. We could do web browsing. Maybe even document editing.
Off-panel voice: Very convenient.
Off-panel voice: Perfect!
Off-panel voice: We have a winner!
Title: 40 Million Credit Cards -- I.
Voice from door: We'll choose between point-of-sale models A and B.
Voice from door: At stake: security of 40 million credit cards. Maybe up to 110 million.
The next panel shows a number of people sitting at a circular table. In order from left to right, they are: man 1, man 2, woman 1, man 3, and woman 2.
Man 1: Model A uses open source. We can look inside and examine it for security issues.
Woman 2: So can the hackers?
Man 1: Excellent point. Sadly, yes.
The conversation continues across several panels.
Man 1: A boots into cryptographically-signed point-of-sale software. It allows no external programs.
Woman 1: How do we run an antivirus program?
Man 1: We can't.
Woman 1: Unacceptable.
Man 1: The other alternative is Model B. It uses tightly closed software. Nobody can look inside it. Not even us.
Man 2: Good. No hacker will ever figure out how to make a virus for Model B.
Man 1: There are several antivirus products on the market for Model B. That guarantees ironclad security.
Man 2: Great!
Woman 2: Excellent!
The next and final panel shows only man 1.
Model B lets us run any program on it. We could do web browsing. Maybe even document editing.
Off-panel voice: Very convenient.
Off-panel voice: Perfect!
Off-panel voice: We have a winner!
Title: 40 Million Credit Cards -- I.